Database SSH Tunneling
DataSiv enables you to connect to databases behind VPNs and firewalls using ssh tunneling.
To begin, when creating a new Sql Api Resource, set Ssh Tunnel to true.
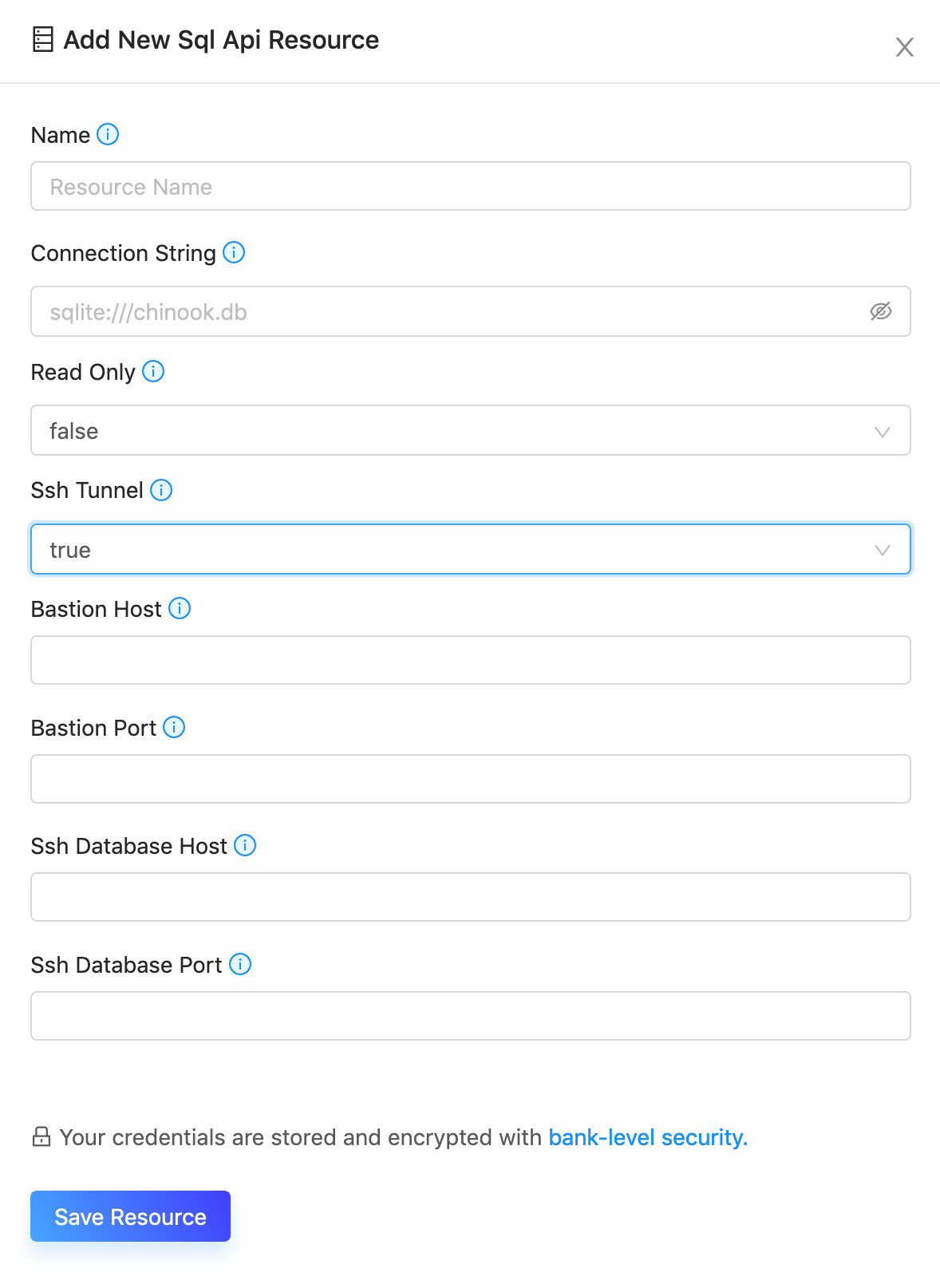
Provide the bastion host, bastion port, the ssh database host and ssh database port as specified.
Leave {host} and {port} placeholders in the SQL connection stringIn the connection string, please leave placeholder constants
{host}and{port}. We will substitute those parameters when connecting to your database via ssh tunneling.
Adding DataSiv's public key
DataSiv will attempt to ssh using the user datasiv. Below is a sample script to run for Ubuntu adapted from https://aws.amazon.com/premiumsupport/knowledge-center/new-user-accounts-linux-instance/
ec2-user@bastion:~$ sudo adduser datasiv --disabled-password
Adding user `datasiv' ...
Adding new group `datasiv' (1003) ...
Adding new user `datasiv' (1003) with group `datasiv' ...
Creating home directory `/home/datasiv' ...
Copying files from `/etc/skel' ...
Changing the user information for datasiv
Enter the new value, or press ENTER for the default
Full Name []:
Room Number []:
Work Phone []:
Home Phone []:
Other []:
Is the information correct? [Y/n] yNext, download DataSiv's public key from here and add it to your public keys:
# Login as datasiv
sudo su - datasiv
# Create the authorized_keys file if it does not exist yet
mkdir .ssh
touch .ssh/authorized_keys
chmod 700 .ssh
# Use your favorite editor to add DataSiv's public key to the file
vim .ssh/authorized_keys
# Set permissions on the authorized_keys file
chmod 600 .ssh/authorized_keysYou should now be able to connect to your database via SSH tunneling.
For specific information on how to connect to an AWS RDS instance with SSH tunneling via an EC2 instance, please see https://aws.amazon.com/premiumsupport/knowledge-center/rds-connect-ec2-bastion-host/.
Make sure to whitelist inbound requests from your bastion's internal IP to the databaseIf you're using AWS, make sure to add the internal IP of your EC2 bastion instance and database port to the security group of your database.
Leave {host} and {port} placeholders in the SQL connection stringIn the connection string, please leave placeholder constants
{host}and{port}. We will substitute those parameters when connecting to your database via ssh tunneling.
For example, if you're connecting to an RDS instance via an EC2 instance, your resource may look something like this:
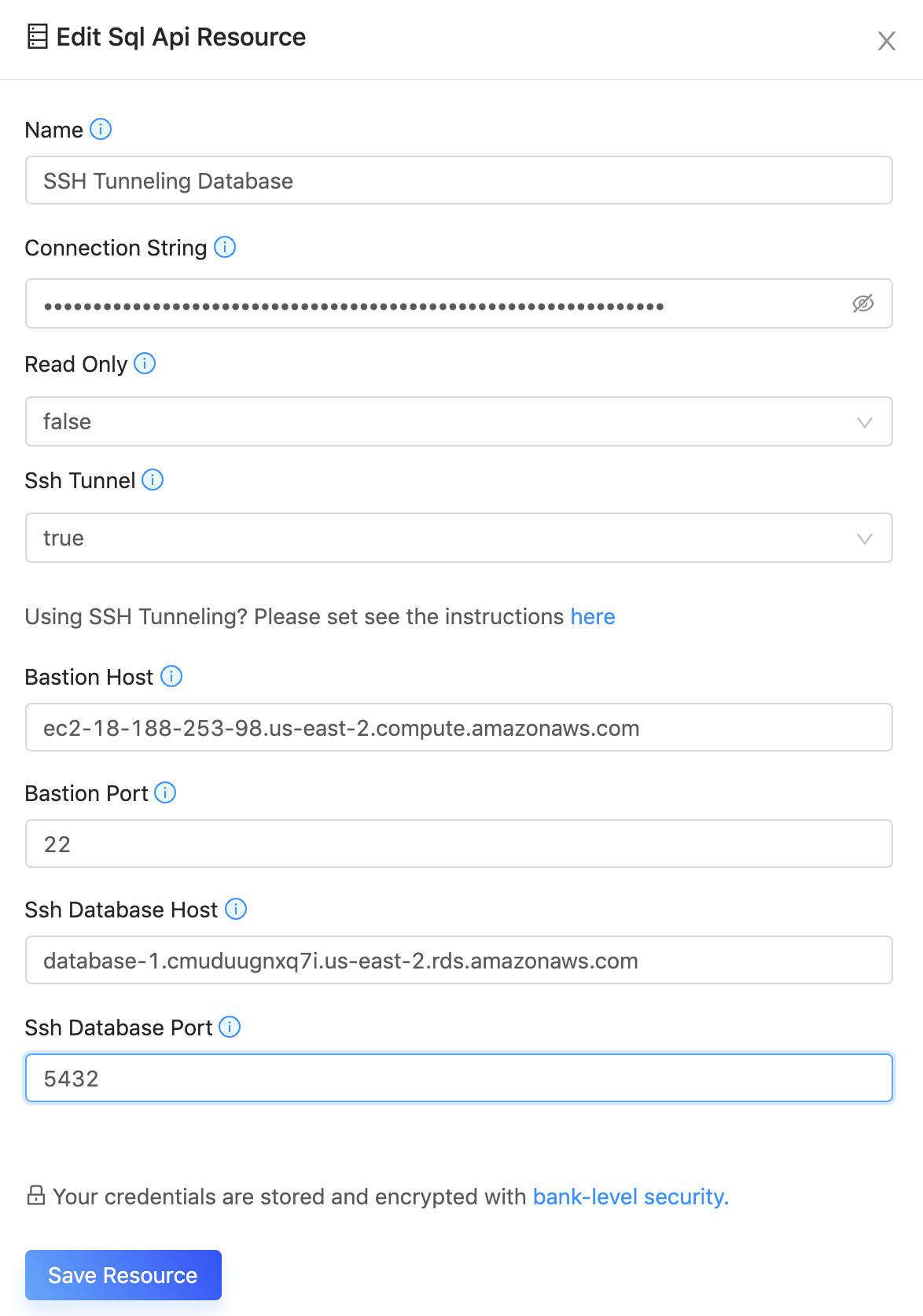
Troubleshooting
If you get the error: server closed the connection unexpectedly. This probably means the server terminated abnormally before or while processing the request
This probably means you haven't whitelisted incoming traffic from your bastion to your database.
If you get the error: Could not establish session to SSH gateway
This probably means you haven't set up proper SSH tunneling into your bastion.
Updated 8 months ago
